AWS Cloud Migration Enhance your business efficiency and agility with...
Read MoreThis blog lists one of the Architecture design, ‘AWS site to site VPN in control tower’, which we did for a client for connecting ON premise to AWS environment in a control tower environment.
For connecting on-prem networks with AWS, AWS Transit gateway-based approach is considered. This approach takes advantage of an AWS-managed VPN endpoint for connecting to multiple VPCs in the same region without the additional cost and management of multiple IPSec VPN connections to multiple Amazon VPCs.
In this article, we would discuss the site-to-site VPN and different options we explored for site-to-site VPN using
Transit gateway and Egress options can be used.
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources into a virtual network that you’ve defined. This virtual network closely resembles a traditional network that you’d operate in your own data center. It provides the benefits of using the scalable infrastructure of AWS. Each VPC can further be set up with different options to make the environment more secure
AWS Transit Gateway is an AWS-managed high availability and scalability regional network transit hub used to interconnect VPCs and customer networks using the route tables. AWS Transit Gateway + VPN, using the Transit Gateway VPN attachment, provides the option of creating an IPsec VPN connection between your remote network and the Transit Gateway over the internet.

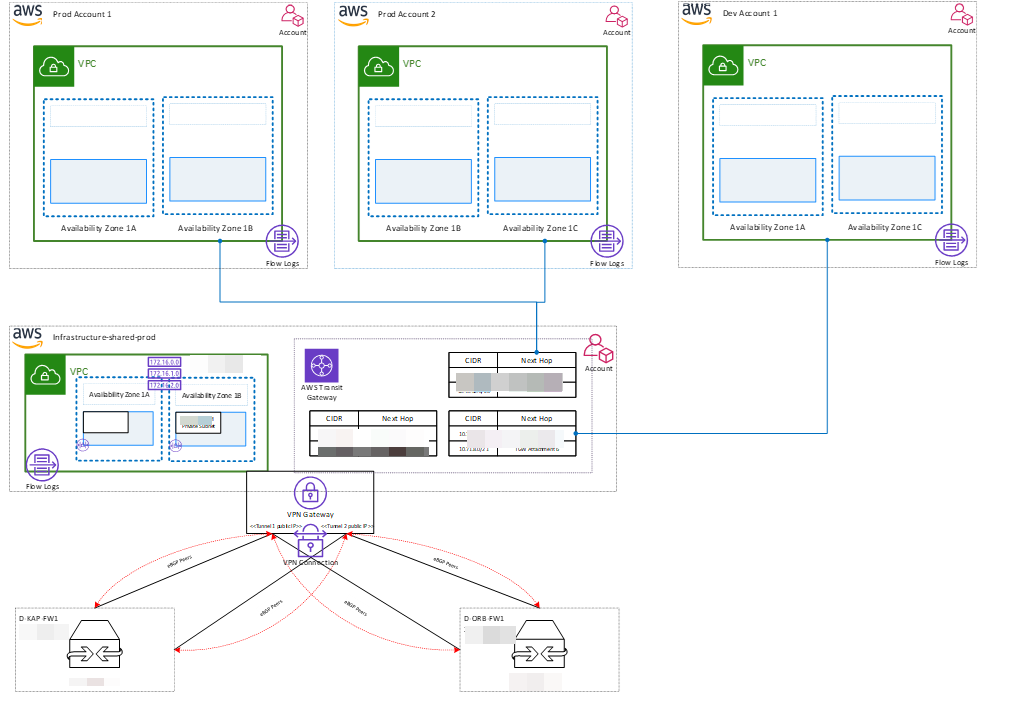
Figure 1: AWS Transit Gateway with Redundant VPN
This provides an optimum way to connect multiple VPC endpoints to an on-prem network. With the AWS Control Tower in place, the account you create will be for projects/applications. Each of these accounts will have a separate VPC and these can be connected to a transit gateway running in the infrastructure account to provide on-prem connectivity if required.
We will be using dynamic routing between the on-prem firewalls and AWS Transit Gateway.
In the client’s AWS environment, a transit gateway will be created in the Infrastructure-shared-prod account, which will provide connectivity between different Spoke VPCs as well as connectivity with the on-prem network.
So helps to connect multiple VPCs together.
There are 2 separate network zones considered for Production and Dev accounts. These will have separate route tables in the transit gateway to provide network isolation between Production and Dev.
The below diagram shows the connectivity between the transit gateway and different route tables for production and dev/sandbox accounts.
You can manage the transit gateway in control tower accounts easily so it can talk to different accounts, and each can talk to the transit gateway. In this case, we have kept a single one for Dev and production instance
In this case, client was not looking for a segregated approach hence this works to keep it as a single Transit gateway
If you set up multiple transit gateway it requires that many setups of gateway and monitoring to be done. Hence can be easily managed if you are just starting out or for POC or a new product launch until it grows.
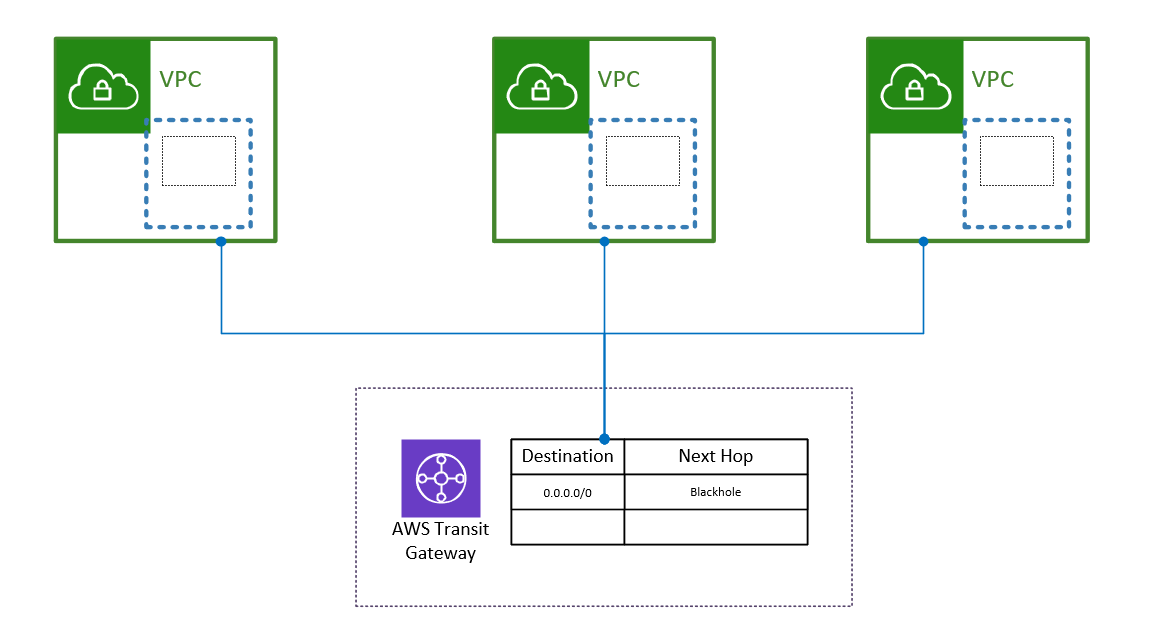
This is to manage the Traffic which is send out from the VPC account
For the outbound internet traffic, below we consider options for different phases and will carry out the basis of the client’s network requirements.
Here we added Egress VPC to another account. We do this to avoid deploying a NAT Gateway in every spoke VPC, which can become expensive, so centralizing it is a viable option. To centralize, we will create an egress VPC in the shared network account. Then route all egress traffic from the spoke VPCs via a NAT Gateway sitting in this VPC leveraging Transit Gateway. The router table which sends all traffic to Egress VPC which further manages all inbound and outbound communication to internet.
This phase will implement when there are significant workloads, and the intermediate solutions will need to get the scale to support the growing infrastructure/network traffic.
When you attach a VPC to a transit gateway, any resources in Availability Zones where there is no transit gateway attachment cannot reach the transit gateway. If there is a route to the transit gateway in a subnet route table, traffic is forwarded to the transit gateway only when the transit gateway has an attachment in a subnet in the same Availability Zone.
Figure 6: Centralized egress model
So with this, we conclude the multiple options and a phase-wise approach you could use to get a start with On-premise Connectivity to your AWS environment. This is specific to the use of a control tower and helps to get a start with a less restricted approach.
Looking for help to manage your AWS infrastructure and get a review, please come and talk to us for more details in report.
References
AWS Cloud Migration Enhance your business efficiency and agility with...
Read MoreAWS API Gateway Competency Enhance your business efficiency and agility...
Read MoreAWS DevOps Competency Transform your business efficiency and agility...
Read More