AWS Environment Setup For Tonkin + taylor
Executive Summary
About Client
AWS Environment Setup
Tonkin + Taylor is New Zealand’s leading environment and engineering consultancy with offices located globally. They shape interfaces between people and the environment which includes earth, water and air. They have won awards like Beaton Client Choice Award for Best Provider to Government and Community-2022 and IPWEA Award for Excellence in Water Projects for the Papakura Water Treatment Plan- 2021.
https://www.tonkintaylor.co.nz/
Location: New Zealand
Project Background
Tonkin + Taylor were embarking on the journey for launching a full suite of digital product and zeroed upon AWS as thier choice for cloud environment. They wanted to create new applications and migrate to cloud services to improve their scalability, ensure availability, minimize latency and reduce costs. They were also looking to accelerate their digital transformation and add greater business value through AWS Development Environment best practices. Lastly with the new apps they wanted to monetize and create SAAS based offerings for the end users. For all this it was needed to do AWS Environment Setup which follows best practices and meets compliance which can be used as a base for implementing more applications.
Scope & Requirement
In the 1st Phase of the AWS Environment Setup, implementation was discussed as follows:
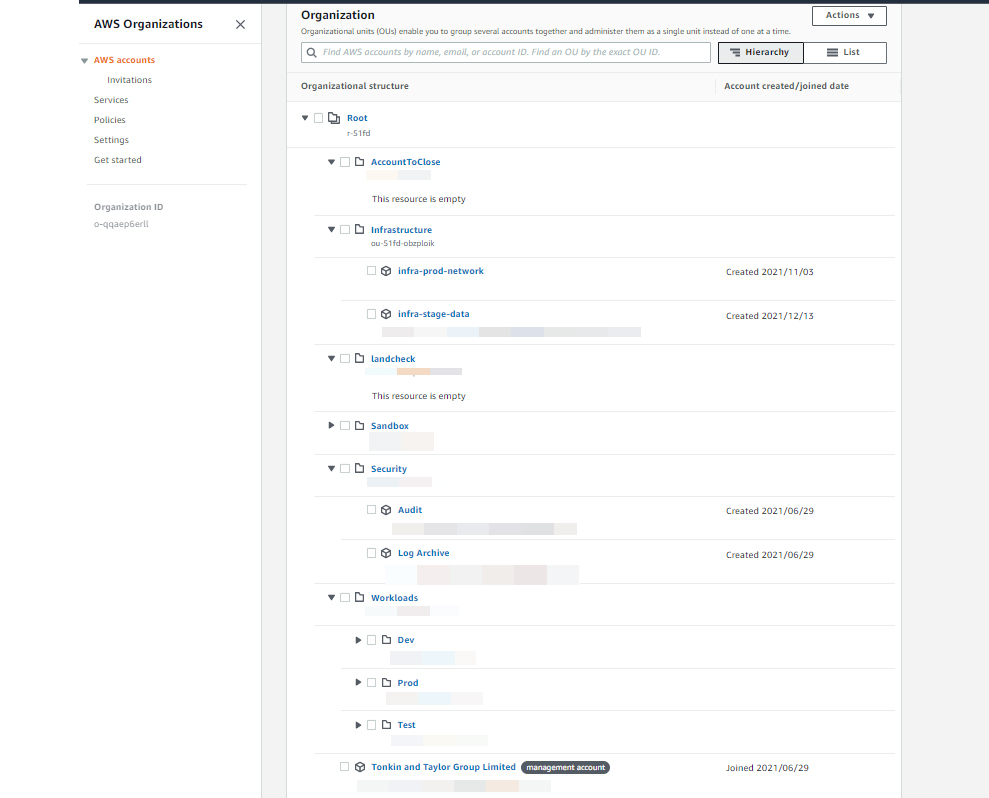
- Setting up AWS environment for multi account, Multi environment setup
- Ensure the all AWS accounts follow same set of policies and adhering to all legal and regulatory compliance.
- Setup connectivity between different AWS accounts and on-prem network
- Setup AWS security hub to provide a comprehensive view of security state
Implementation
Technology and Architecture
Read more on the key components which defined the Architecture for AWS Environment Setup for Tonkin + Taylor
Technology/ Services used
We used AWS services and helped them to setup below
- Cloud: AWS
- Organization setup: Control tower
- AWS SSO for authentication using existing AzureAD credentials
- Policies setup: Created AWS service control policies
- Templates created for using common AWS services
Security & Compliance:
- Tagging Policies
- AWS config for compliance checks
- NIST compliance
- Guardrails
- Security Hub
Network Architecture
- Site to Site VPN Architecture using Transit Gateway
- Distributed AWS Network Firewall
- Monitoring with Cloud Watch and VPC flow logs.
Backup and Recovery
- Cloud systems and components used followed AWS’s well-Architected framework and the resources were all Multi-zone availability with uptime of 99.99% or more.
Cost Optimization
- Alerts and notifications are configured in the AWS cost
Code Management, Deployment
- Cloudformation scripts for creating stacksets and scripts for generating AWS services was handed over to the client
Challenges of AWS Environment Setup
- It was a bit of a challenge to ensure the new environment meets all of the compliance criteria and still remain cost effective.
- As per best practices we need to have a set of Unique machines and each may need to have its own VPC but that may incur a cost to the client. So we discussed and agreed for a specific 75% to be achieved which would be deemed as acceptable
- We have some non compliance being generated by standard AWS services
- We got below feedback from AWS support . “It was reported that there are some policies and roles which are created by control tower and are created using best practices and there is no harm or security issue which arises it. Sometimes the conformance pack you use does shows the by default created policies to be non-compliant and you can ignore that for the time being. To make it compliant we have to either delete or the modify these roles/policies and since these roles and policies managed by the Control Tower, it is recommended not to manually update/delete the roles attached. Diving deeper into the issue, I could refer that the Control Tower managed artifacts feature heavily on the compliance failure list and there is no way to specifically exclude Control Tower managed artifacts from the compliance checking. Checking further with the internal team, I found that they are aware of the issue and there has been an ongoing feature request to exclude Control Tower managed artifacts from the compliance checking to avoid these such security findings. ” So based on this feedback we ensured to make a note that the non compliance being shown may not be an accurate one and these would be treated as exceptions.
Project Completion
Duration
Oct 2021 to Dec 2021 ~ 3 months
Deliverables
- Implemented AWS Control tower with Org Unit structure and Service control policies
- Implemented AWS Config with NIST conformance pack
- Implemented AWS Security Hub
- Implemented Site to Site VPN using AWS Transit Gateway
- Handover and Support documents were provided
Support
- 1 month extended support
- A template for Cloud formation stack to create more AWS resources using the available stacks
- Screen sharing sessions with demo of how the services and new workloads can be deployed.
Testimonial
After we setup and enabled client to start using the newly built environment they were eager to get apps being rolled out using cloud resources. It was exciting to see client using the environment extensively. We also took Feedback from stakeholders as below:

Tonkin + Taylor has initiated its Digital Transformation journey and AWS is one of the key partner in its effort to enable a Digital savvy organization that provides an excellent Customer and Employee Experience. As part of this journey, we have received great support in Peritos as our AWS Partner. The team at Peritos are knowledgeable, bring previous experience of enabling other organizations on this journey, great with quality and timeliness of delivery. T+T has setup its AWS platform with support of AWS and Peritos and has enabled us to provide our Engineers and clients an environment for data ingestion, transformation and hosting of multiple applications, analytics, data science & visualization.
Santosh Dixit
Digitization delivery lead
Next Phase
We are now looking at the next phase of the project which involves:
1. Launching new digital products with the help of AWS environments which have been setup
2. Any adhoc change requests for managing the cloud environment